At its I/O 2016 keynote, Google announced a new messaging, chatbot-enabled app called Allo. In the aftermath of Allo’s reveal, a furor of controversy erupted surrounding how private the new messaging platform’s sensitive conversion data really is.
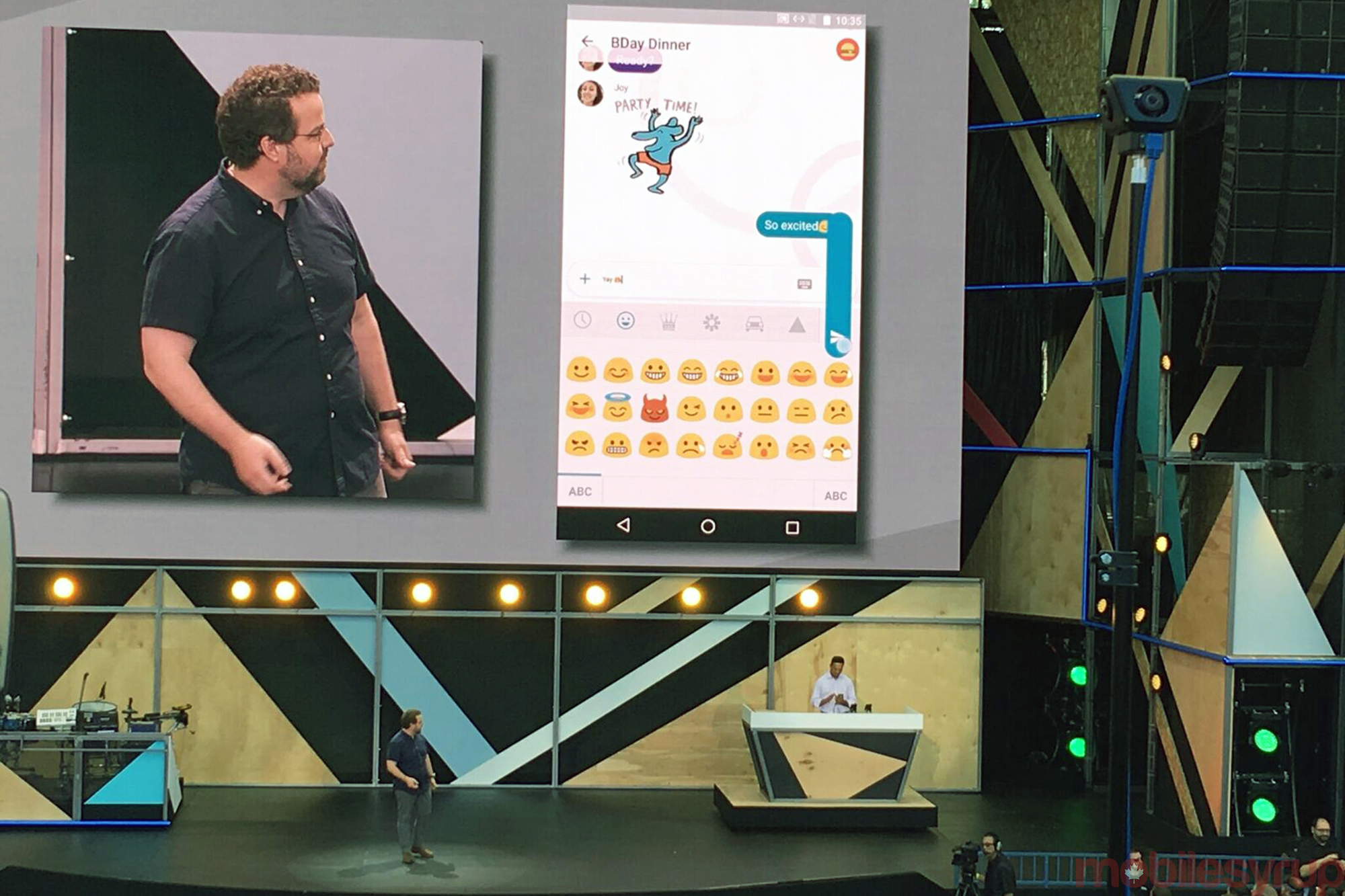
It’s easy to be impressed by Allo. The app features a slick user interface, custom sizing for text and emojis, and is Google’s first chat application to offer a form of end-to-end encryption, a positive step in the right direction for privacy-concerned Android users.
Google's decision to disable end-to-end encryption by default in its new #Allo chat app is dangerous, and makes it unsafe. Avoid it for now.
— Edward Snowden (@Snowden) May 19, 2016
What’s important to note, however, is Allo’s end-to-end encryption is only present when using the app in incognito mode, something Google touted during its I/O’s keynote, resulting in the overall messaging platform not being as secure as some might assume.
The main draw of Allo is Google Assistant, a Siri, Cortana and Alexa competitor that gives users personalized answers to questions, and is also closely integrated with Google Home, the Mountain View, California tech giant’s recently revealed, always-listening Amazon Echo competitor.
Allo’s most interesting feature, which drew cheers from the crowd of journalists and developers attending I/O’s keynote, is its ability to utilize Google Assistant to offer customized, suggested replies to friends and family members. In order for this feature to work, however, Allo is always reading every user’s messages, carefully analyzing the contents with machine-learning algorithms in order to create canned responses that make sense.
This means that when using Allo, Google has access to conversations and messages at all times, a point Motherboard staff writer Jason Koebler also makes in a recent story.
Some will likely point out that Google’s Allo also features an incognito browsing mode focused on privacy, a feature many Android and mobile enthusiast websites have written about since the app’s initial reveal. Many have lauded Google for including this feature in Allo, because, in theory, hackers, government officials and law enforcement will not be able to access conversations within the app. But what Google didn’t make clear during its I/O keynote, is this encryption only exists when incognito is active.
The average Allo user likely won’t take this additional step when using the new messaging app, similar to how most people aren’t aware it’s possible to browse Chrome, as well as other browsers, in incognito mode. In fact, Google is probably hoping most users won’t take advantage of this feature given Allo is designed to be used without incognito mode turned on (this is how the canned messaging system works). While we don’t know for certain yet, data gathered through Allo will probably be used to target the chat app’s users with advertisements, similar to Google’s popular Chrome browser.
Following Allo’s announcement, Open Whisper Systems released a blog post detailing its recent work with Google to bring the company’s Signal Protocol to the Allo’s incognito mode. This indicates that the same encryption technology powering WhatsApp is also behind Allo, though only the Google-developed app’s incognito mode.
In comparison, all WhatsApp messages feature end-to-end encryption and do not ask users engage a specific incognito mode. To be clear, however, Allo is far from the only chat app to suffer from encryption-related issues.
Allo is slated to launch later this summer. Pre-registration for the new messaging platform is open now, though not to Canadians.
[source]Google[/source][via]Motherboard, Whisper[/via]
MobileSyrup may earn a commission from purchases made via our links, which helps fund the journalism we provide free on our website. These links do not influence our editorial content. Support us here.