Earlier this month, security researcher and former Google employee Felix Krause published a report detailing how Instagram, Facebook, and other apps can use the in-app browser to track people’s online behaviour. Now Krause is back with a tool that can help show users the extent of this tracking.
Here’s a quick explainer in case you missed Krause’s original report. Many apps feature a built-in web browser that opens links users click in the app. Krause highlights apps from Meta, like Facebook and Instagram, in the report, but many other apps do this too. (Tiktok is one of the more egregious – Krause claims TikTok can monitor all keyboard inputs and taps in its custom browser, but the company told Forbes it only uses the JavaScript in question for debugging.)
It’s worth noting that not all in-app browsers are bad. While some apps use custom in-app browsers, others use Apple’s Safari. Twitter, Reddit, Gmail, and other apps rely on Safari or the ‘SFSafariViewController’ to open websites in apps. Krause offers a list of apps that do this, noting that they are “on the safe side” as there’s no way for apps to inject code. Android offers a ‘Custom Tab’ feature that leverages users’ default browser, if it supports Custom Tabs, to load websites inside of apps. It’s not clear if JavaScript injections similarly impact this.
On the one hand, this probably shouldn’t come as a huge surprise to most people. If apps track what you’re doing in the app, why would that change for the in-app browser? On the other, this could serve as a wake-up call for some and, hopefully, encourage some action to prevent this tracking. That could come from those in control of app stores (for example, Apple could adjust its guidelines to prevent this kind of behaviour or perhaps extend its App Tracking Transparency feature to cover this kind of behaviour).
More likely, users will be on their own to protect themselves. The best way is to avoid using an in-app browser — thankfully, most apps include an option to use the default browser instead, which means whatever link you click will open in your actual browser, not the in-app option.
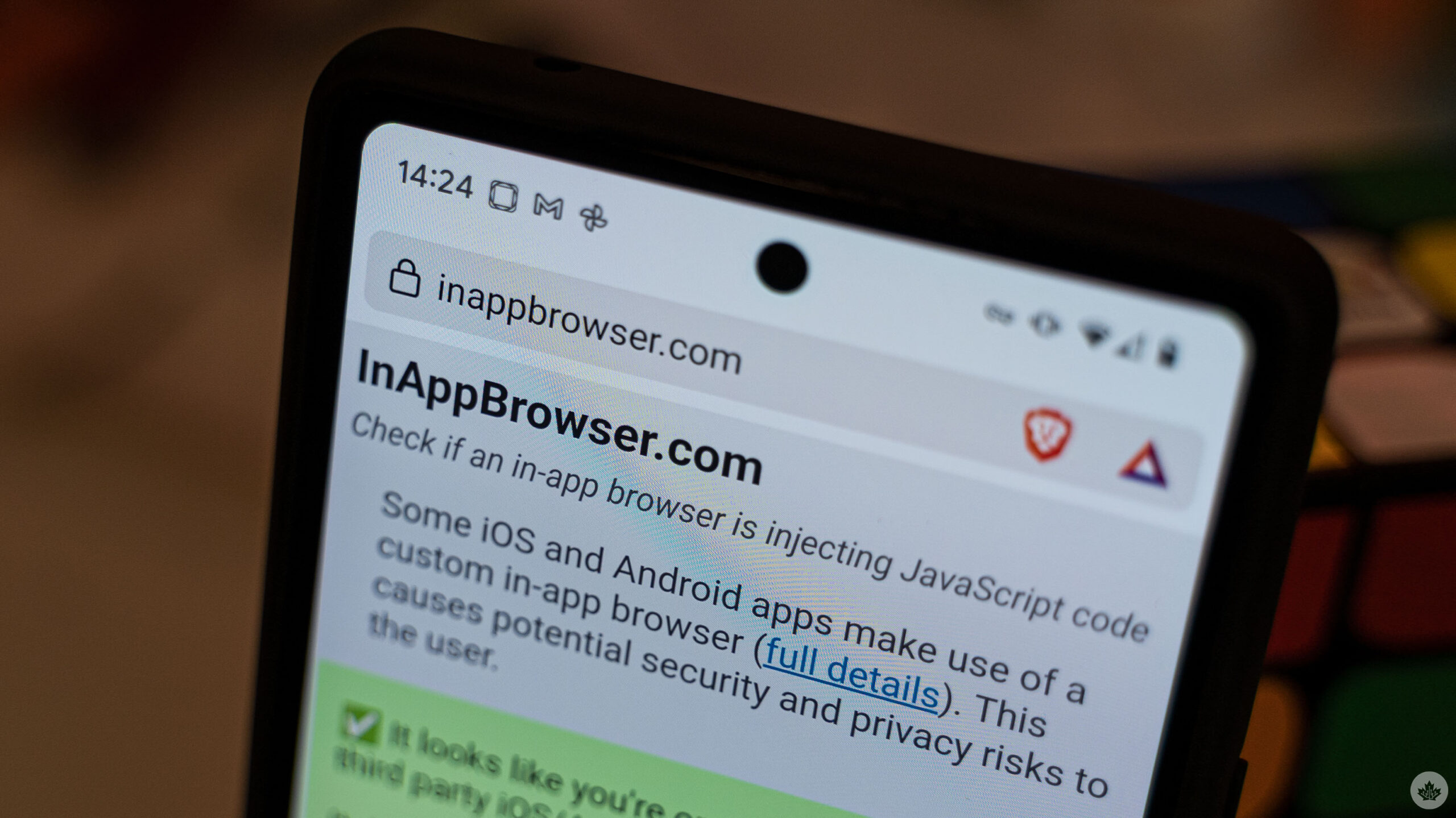
Another thing you can do? Test which apps inject JavaScript into the in-app browser using Krause’s new tool. Called ‘inappbrowser.com,’ it’s a website users can open that will detect JavaScript injections. There are, of course, limitations. The inappbrowser.com tool can’t detect all JavaScript commands that are executed, and just because JavaScript is present doesn’t mean something malicious is happening.
Still, running the inappbrowser.com test could let you know if an app is injecting JavaScript and if it is, that could mean it’s tracking something. To use the tool, navigate to ‘inappbrowser.com’ with an in-app browser. The trick, of course, is to get there — most in-app browsers don’t let you type in a URL. Instead, you have to click the link within the app you want to test. For example, you could post a comment with the link and click it or send a DM to yourself.
You can learn more about in-app browser tracking here.
Source: Felix Krause Via: The Verge
MobileSyrup may earn a commission from purchases made via our links, which helps fund the journalism we provide free on our website. These links do not influence our editorial content. Support us here.


